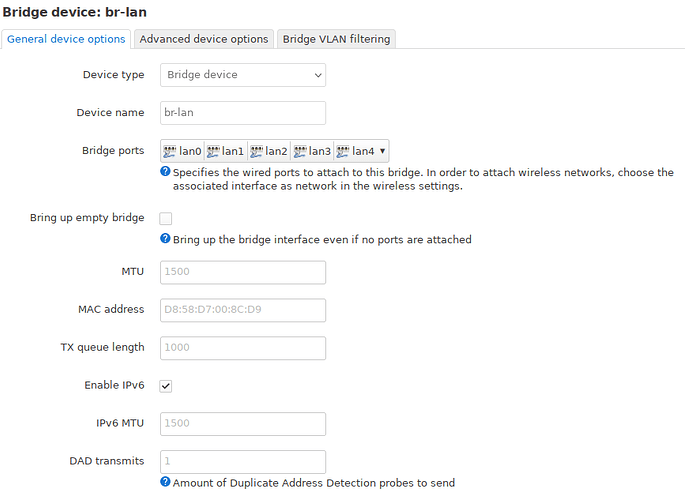
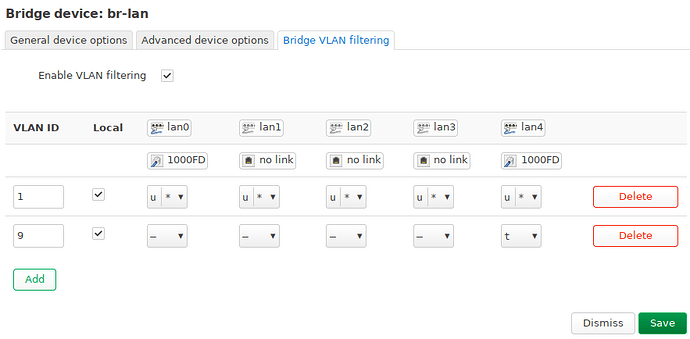
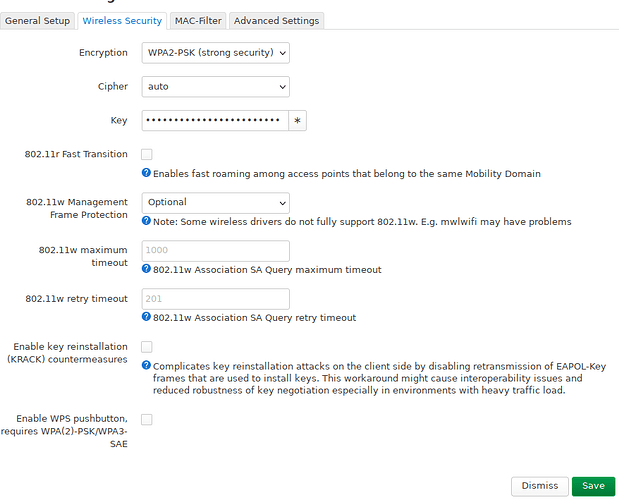
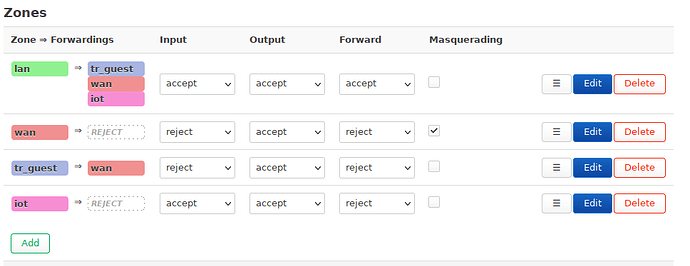
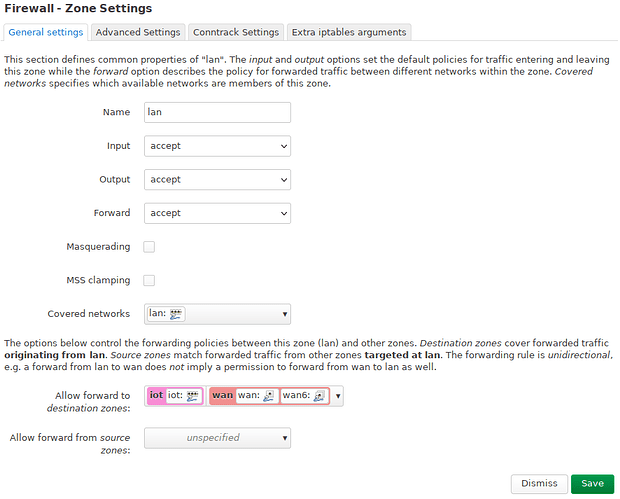
Okay, the “good” news, it seems to be more consistent now. Now no device on a wireless network can talk to any wired device or the router itself when I use VLAN. Here are my configurations. The br-lan device:
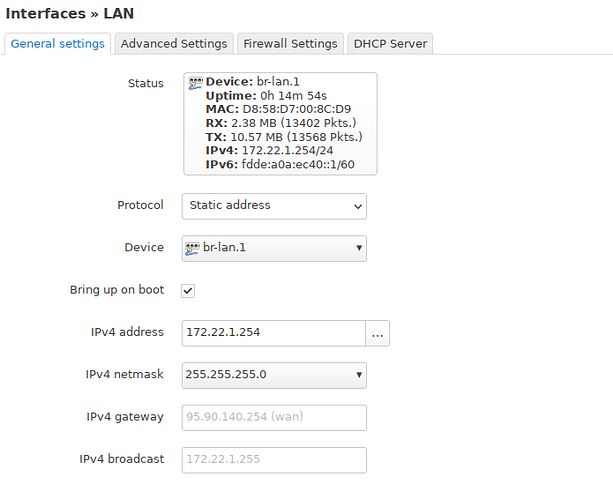
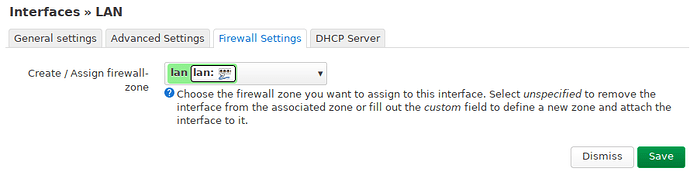
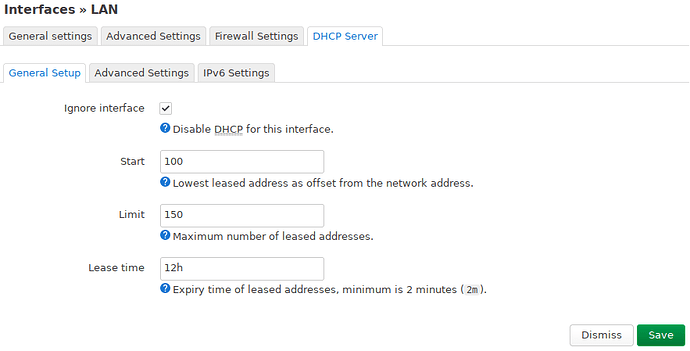
The LAN interface:
The DHCP server for this interface is running on 172.22.1.1 which is connected to br-lan.1.
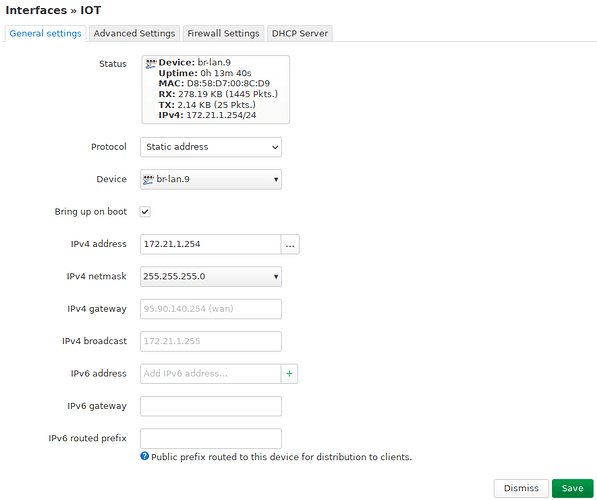
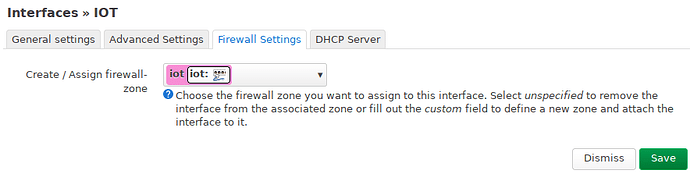
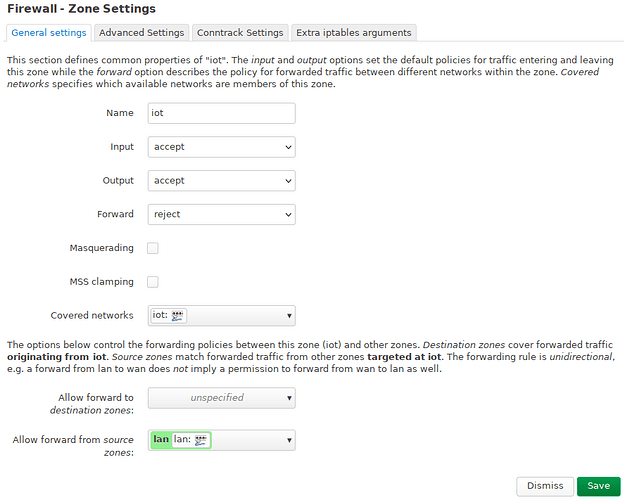
The IOT interface:
This network is statically configured and doesn’t provide DHCP. I could not connect to the LAN network via Wifi since DHCP didn’t go through. It works without VLAN.
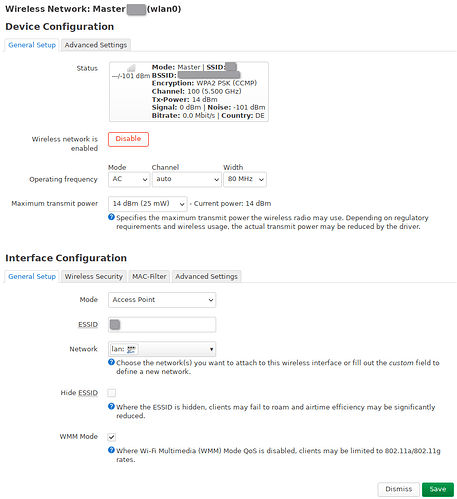
The wifi networks (I will only cover one of each network. The LAN network has multiple Wifi networks but they all behave the same (and are identically configured, except 2.4/5GHz and SSID/key).
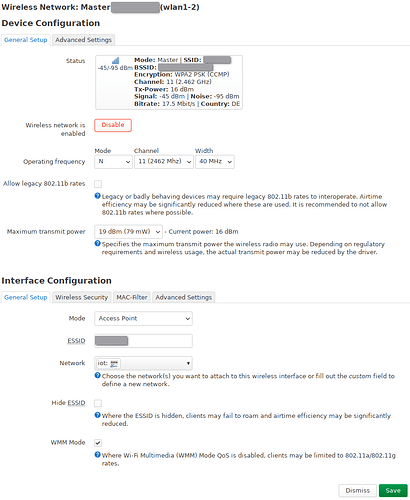
LAN wifi:
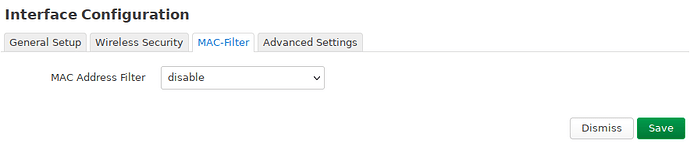
IOT wifi:
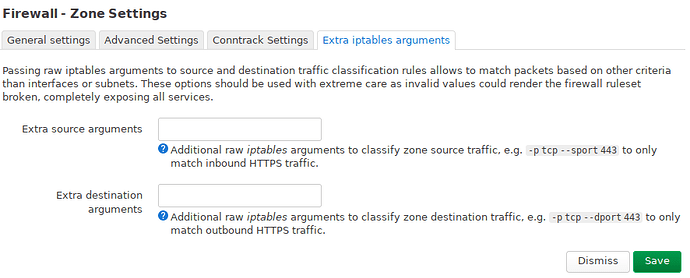
And my firewall configuration. Nothing special here:
lan:
iot:
the other three tabs are identical to lan
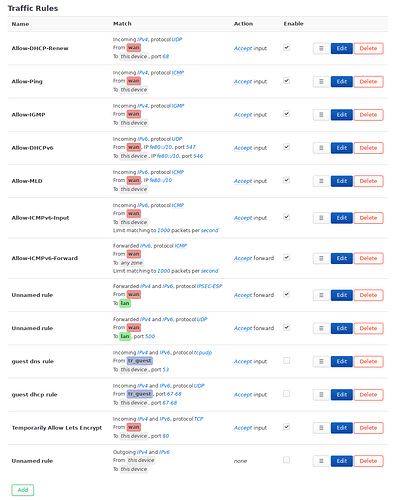
These are the traffic rules, I don’t think I changed anything here from the default:
Other than that no custom rules, no NAT rules, no enabled port forwards.
That being said the VLAN itself works fine. I can confirm a working communication on both the tagged and the untagged VLAN via ethernet. I just cannot reach the wifi networks (and vice versa) from the VLAN (or even from the router itself).
These are my interfaces and routes:
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1024
link/ether xxx brd ff:ff:ff:ff:ff:ff
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1508 qdisc mq state UP group default qlen 1024
link/ether xxx brd ff:ff:ff:ff:ff:ff
inet6 fe80::da58:d7ff:fe00:8cd9/64 scope link
valid_lft forever preferred_lft forever
4: eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1024
link/ether xxx brd ff:ff:ff:ff:ff:ff
inet xxx/24 brd xxx scope global eth2
valid_lft forever preferred_lft forever
5: ip6tnl0@NONE: <NOARP> mtu 1452 qdisc noop state DOWN group default qlen 1000
link/tunnel6 :: brd :: permaddr 21e:55d2:9749::
6: sit0@NONE: <NOARP> mtu 1480 qdisc noop state DOWN group default qlen 1000
link/sit 0.0.0.0 brd 0.0.0.0
7: lan0@eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP group default qlen 1000
link/ether xxx brd ff:ff:ff:ff:ff:ff
8: lan1@eth1: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue master br-lan state LOWERLAYERDOWN group default qlen 1000
link/ether xxx brd ff:ff:ff:ff:ff:ff
9: lan2@eth1: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue master br-lan state LOWERLAYERDOWN group default qlen 1000
link/ether xxx brd ff:ff:ff:ff:ff:ff
10: lan3@eth1: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue master br-lan state LOWERLAYERDOWN group default qlen 1000
link/ether xxx brd ff:ff:ff:ff:ff:ff
11: lan4@eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP group default qlen 1000
link/ether xxx brd ff:ff:ff:ff:ff:ff
12: gre0@NONE: <NOARP> mtu 1476 qdisc noop state DOWN group default qlen 1000
link/gre 0.0.0.0 brd 0.0.0.0
13: gretap0@NONE: <BROADCAST,MULTICAST> mtu 1462 qdisc noop state DOWN group default qlen 1000
link/ether 00:00:00:00:00:00 brd ff:ff:ff:ff:ff:ff
14: erspan0@NONE: <BROADCAST,MULTICAST> mtu 1450 qdisc noop state DOWN group default qlen 1000
link/ether 00:00:00:00:00:00 brd ff:ff:ff:ff:ff:ff
17: br-guest_turris: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default qlen 1000
link/ether xxx brd ff:ff:ff:ff:ff:ff
inet 10.111.222.1/24 brd 10.111.222.255 scope global br-guest_turris
valid_lft forever preferred_lft forever
25: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP group default qlen 1000
link/ether xxx brd ff:ff:ff:ff:ff:ff
inet6 fe80::6f0:21ff:fe24:2543/64 scope link
valid_lft forever preferred_lft forever
36: wlan1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP group default qlen 1000
link/ether xxx brd ff:ff:ff:ff:ff:ff
inet6 fe80::6f0:21ff:fe31:8e9f/64 scope link
valid_lft forever preferred_lft forever
37: wlan1-1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP group default qlen 1000
link/ether xxx brd ff:ff:ff:ff:ff:ff permaddr xxx
inet6 fe80::4f0:21ff:fe31:8e9f/64 scope link
valid_lft forever preferred_lft forever
38: wlan1-2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether xxx brd ff:ff:ff:ff:ff:ff permaddr xxx
inet6 fe80::f0:21ff:fe31:8e9f/64 scope link
valid_lft forever preferred_lft forever
39: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether xxx brd ff:ff:ff:ff:ff:ff
inet6 fe80::da58:d7ff:fe00:8cd9/64 scope link
valid_lft forever preferred_lft forever
40: br-lan.1@br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether xxx brd ff:ff:ff:ff:ff:ff
inet 172.22.1.254/24 brd 172.22.1.255 scope global br-lan.1
valid_lft forever preferred_lft forever
inet6 xxx::1/60 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fe80::da58:d7ff:fe00:8cd9/64 scope link
valid_lft forever preferred_lft forever
42: br-lan.9@br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether xxx brd ff:ff:ff:ff:ff:ff
inet 172.21.1.254/24 brd 172.21.1.255 scope global br-lan.9
valid_lft forever preferred_lft forever
inet6 fe80::da58:d7ff:fe00:8cd9/64 scope link
valid_lft forever preferred_lft forever
default via xxx dev eth2 proto static src xxx
10.111.222.0/24 dev br-guest_turris proto kernel scope link src 10.111.222.1 linkdown
xxx dev eth2 proto kernel scope link src xxx
172.21.1.0/24 dev br-lan.9 proto kernel scope link src 172.21.1.254
172.22.1.0/24 dev br-lan.1 proto kernel scope link src 172.22.1.254
Maybe that’s any help.
I hope that gives you some information to work with. I have a workaround (which is not using the TO to provide the IOT wifi network at all) but I’m not really happy with that.