I have a problem with OpenVPN in Turris 4.0
OpenVPN configuration is moved from 3.11.5
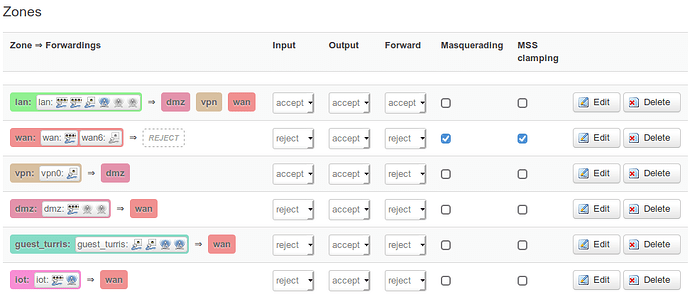
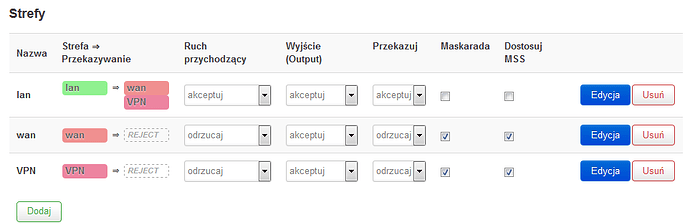
Firewall settings was recreated in Luci.
I’m able to ping all local openvpn interfaces (in vpn zone) from machine in lan zone.
I’m able to ping all remote openvpn interfaces and remote hosts from router.
I’m not able to ping any remote openvpn interface or remote host from machine in lan zone (Destination Port Unreachable)
I assume that problem is in routing / masquerading, but cannot track it.
I’ve tried moving interfaces to WAN zone, but with no effect.
All required routes on Omnia are present.
network
config interface ‘loopback’
option ifname ‘lo’
option proto ‘static’
option ipaddr ‘127.0.0.1’
option netmask ‘255.0.0.0’
config globals ‘globals’
option ula_prefix ‘fd1b:6a2c:65f1::/48’
config interface ‘lan’
option type ‘bridge’
option proto ‘static’
option netmask ‘255.255.255.0’
option ip6assign ‘60’
option bridge_empty ‘1’
list ifname ‘lan0’
list ifname ‘lan1’
list ifname ‘lan2’
list ifname ‘lan3’
list ifname ‘lan4’
option _turris_mode ‘managed’
option ipaddr ‘192.168.9.1’
config interface ‘wan’
option ifname ‘eth2’
option proto ‘dhcp’
option ipv6 ‘0’
config interface ‘wan6’
option ifname ‘@wan’
option proto ‘none’
config interface ‘guest_turris’
option type ‘bridge’
option proto ‘static’
option ipaddr ‘10.111.222.1’
option netmask ‘255.255.255.0’
option bridge_empty ‘1’
option enabled ‘0’
config interface ‘client1’
option proto ‘none’
list ifname ‘tun_client1’
config interface ‘client2’
option proto ‘none’
list ifname ‘tun_client2’
[other client interfaces here]
firewall
config defaults
option syn_flood ‘1’
option input ‘ACCEPT’
option output ‘ACCEPT’
option forward ‘REJECT’
option drop_invalid ‘1’
config zone
option name ‘lan’
option input ‘ACCEPT’
option output ‘ACCEPT’
option forward ‘ACCEPT’
option network ‘lan’
config zone
option name ‘wan’
option input ‘REJECT’
option output ‘ACCEPT’
option forward ‘REJECT’
option masq ‘1’
option mtu_fix ‘1’
option network ‘wan wan6’
config rule
option name ‘Allow-DHCP-Renew’
option src ‘wan’
option proto ‘udp’
option dest_port ‘68’
option target ‘ACCEPT’
option family ‘ipv4’
config rule
option name ‘Allow-Ping’
option src ‘wan’
option proto ‘icmp’
option icmp_type ‘echo-request’
option family ‘ipv4’
option target ‘ACCEPT’
config rule
option name ‘Allow-IGMP’
option src ‘wan’
option proto ‘igmp’
option family ‘ipv4’
option target ‘ACCEPT’
config rule
option name ‘Allow-DHCPv6’
option src ‘wan’
option proto ‘udp’
option src_ip ‘fc00::/6’
option dest_ip ‘fc00::/6’
option dest_port ‘546’
option family ‘ipv6’
option target ‘ACCEPT’
config rule
option name ‘Allow-MLD’
option src ‘wan’
option proto ‘icmp’
option src_ip ‘fe80::/10’
list icmp_type ‘130/0’
list icmp_type ‘131/0’
list icmp_type ‘132/0’
list icmp_type ‘143/0’
option family ‘ipv6’
option target ‘ACCEPT’
config rule
option name ‘Allow-ICMPv6-Input’
option src ‘wan’
option proto ‘icmp’
list icmp_type ‘echo-request’
list icmp_type ‘echo-reply’
list icmp_type ‘destination-unreachable’
list icmp_type ‘packet-too-big’
list icmp_type ‘time-exceeded’
list icmp_type ‘bad-header’
list icmp_type ‘unknown-header-type’
list icmp_type ‘router-solicitation’
list icmp_type ‘neighbour-solicitation’
list icmp_type ‘router-advertisement’
list icmp_type ‘neighbour-advertisement’
option limit ‘1000/sec’
option family ‘ipv6’
option target ‘ACCEPT’
config rule
option name ‘Allow-ICMPv6-Forward’
option src ‘wan’
option dest ‘*’
option proto ‘icmp’
list icmp_type ‘echo-request’
list icmp_type ‘echo-reply’
list icmp_type ‘destination-unreachable’
list icmp_type ‘packet-too-big’
list icmp_type ‘time-exceeded’
list icmp_type ‘bad-header’
list icmp_type ‘unknown-header-type’
option limit ‘1000/sec’
option family ‘ipv6’
option target ‘ACCEPT’
config rule
option name ‘Allow-IPSec-ESP’
option src ‘wan’
option dest ‘lan’
option proto ‘esp’
option target ‘ACCEPT’
config rule
option name ‘Allow-ISAKMP’
option src ‘wan’
option dest ‘lan’
option dest_port ‘500’
option proto ‘udp’
option target ‘ACCEPT’
config include
option path ‘/etc/firewall.user’
config zone ‘guest_turris’
option name ‘guest_turris’
option input ‘REJECT’
option forward ‘REJECT’
option output ‘ACCEPT’
option enabled ‘0’
option network ‘guest_turris’
config forwarding ‘guest_turris_forward_wan’
option name ‘guest to wan forward’
option src ‘guest_turris’
option dest ‘wan’
option enabled ‘0’
config rule ‘guest_turris_dns_rule’
option name ‘guest dns rule’
option src ‘guest_turris’
option proto ‘tcpudp’
option dest_port ‘53’
option target ‘ACCEPT’
option enabled ‘0’
config rule ‘guest_turris_dhcp_rule’
option name ‘guest dhcp rule’
option src ‘guest_turris’
option proto ‘udp’
option src_port ‘67-68’
option dest_port ‘67-68’
option target ‘ACCEPT’
option enabled ‘0’
config rule ‘wan_ssh_turris_rule’
option name ‘wan_ssh_turris_rule’
option enabled ‘0’
option target ‘ACCEPT’
option dest_port ‘22’
option proto ‘tcp’
option src ‘wan’
config rule ‘wan_http_turris_rule’
option name ‘wan_http_turris_rule’
option enabled ‘0’
option target ‘ACCEPT’
option dest_port ‘80’
option proto ‘tcp’
option src ‘wan’
config rule ‘wan_https_turris_rule’
option name ‘wan_https_turris_rule’
option enabled ‘0’
option target ‘ACCEPT’
option dest_port ‘443’
option proto ‘tcp’
option src ‘wan’
config rule ‘turris_wan_6in4_rule’
option enabled ‘0’
[redirects]
config zone
option forward ‘REJECT’
option output ‘ACCEPT’
option name ‘VPN’
option input ‘REJECT’
option masq ‘1’
option mtu_fix ‘1’
option network ‘client1 client2 etc…’
config include ‘bcp38’
option type ‘script’
option path ‘/usr/lib/bcp38/run.sh’
option family ‘IPv4’
option reload ‘1’
config include ‘miniupnpd’
option type ‘script’
option path ‘/usr/share/miniupnpd/firewall.include’
option family ‘any’
option reload ‘1’
config forwarding
option dest ‘VPN’
option src ‘lan’
config forwarding
option dest ‘wan’
option src ‘lan’